« Previous 1 2 3 4 Next »
Protect Hyper-V with on-board resources
Counterintelligence
Separate Networks for Hyper-V
You should always operate Hyper-V hosts on separate networks. On the server, use dedicated network adapters to manage the Hyper-V host and connect the VMs. You will also want to use a hardened network to access the VM configurations and the virtual hard disk files. The same applies to live migration.
Generally, IPsec is the best choice for these networks. For communication with file shares, it is best to use SMB 3.0 with end-to-end encryption to prevent man-in-the-middle attacks. If you use different networks, you can secure individual areas more strongly and use the firewall settings to define various rules that restrict access to the respective network adapter.
Best Practices Analyzer
In Windows Server 2019, Microsoft enhanced automatic server role auditing by introducing the Best Practices Analyzer (BPA) built-in tool, which is also available in the Server Manager for checking server roles over the network. Almost all server roles can be tested and the results displayed centrally. The BPA is particularly interesting for Hyper-V, because it can be used to optimize both local and virtual servers. Virtual network switches can also be scanned with the BPA. To start a scan for Hyper-V, enter:
Invoke-BpaModel -ModelId Microsoft/Windows/Hyper-V
You can redirect the results of the scan to a specific path, but you have to create it first:
Invoke-BpaModel -ModelId Microsoft/Windows/Hyper-V -RepositoryPath C:\temp\BPA
If you want to start a scan for a server on the network, use the command:
Invoke-BpaModel -ComputerName dl20 -ModelId Microsoft/Windows/Hyper-V
The results files are stored in XML format in a path you specify, sorted into subdirectories by server role and server. The files can also be parsed in the browser or by other programs. The scan results are stored on the local server – even if you scan a Hyper-V host on the network. For example, if you want to display all scan results for Hyper-V in the PowerShell, use:
Get-BpaResult -ModelId Microsoft/Windows/Hyper-V
If you saved the results in a specific directory, the command
Get-BpaResult -ModelId Microsoft/Windows/Hyper-V -RepositoryPath C:\temp\BPA
will help. You can also export the results to an HTML file:
Get-BpaResult -ModelId Microsoft/Windows/Hyper-V | ConvertTo-Html | Out-File C:\temp\BPA\results.htm
Of course, the results are also available in the GUI. Once you have started the BPA check, you will see the results on the individual tiles in the Server Manager. You can open them by clicking on a tile. If you click on the results of the BPA check, the Server Manager displays the errors that were identified. You can also view all errors from all servers on the network.
From the context menu of a result, you can start a new check for the corresponding server, hide the result, or copy it to the clipboard (e.g., for an Internet search). The BPA results can also be found in the Local Server and All Servers views in the Best Practices Analyzer area of the Server Manager (Figure 2). When a BPA result is displayed for a server role on one of the servers, the tile color changes, which means you can immediately see where improvements for a server are possible. By excluding a result, you can disable individual messages, if required. From the view in the BPA, you can also filter the results by severity, server, and categories.
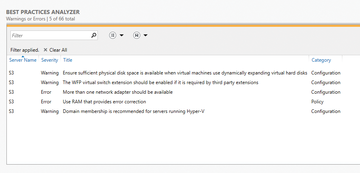 Figure 2: The Best Practices Analyzer examines your server environment and gives you tips for more security.
Figure 2: The Best Practices Analyzer examines your server environment and gives you tips for more security.
Defender Credential Guard and Shielded VMs
To further secure Hyper-V, Microsoft also recommends using advanced security technologies. On Hyper-V servers, you should consider running Windows Defender Credential Guard [5], which uses virtualization-based security to protect credentials. In this way, only defined system software can access credential data; NTLM authentication protocol password hashes, Kerberos tickets, and domain credentials are protected. The configuration is policy based.
You will also want to operate Hyper-V hosts as a guarded fabric, encrypt the VMs, and deploy them as shielded VMs, which provides significantly more security on the network, even if the configuration is more complex.
In Windows Server 2016, Microsoft introduced the Host Guardian Service (HGS) to improved the security of VMs. Virtual servers can be hardened in Hyper-V and isolated from other administrators, attackers, and unauthorized access. Locked-out administrators can still control certain VMs (i.e., shut them down or start them), but they no longer have access to the VM's data, which also applies to unauthorized users or malware. Networks that have been hijacked by attackers or on which other areas have been compromised no longer pose a threat to secured VMs.
The HGS ensures that VMs in Hyper-V are better isolated from each other. If an attacker or malware compromises a VM, this service prevents the attack and the spread to other VMs. Additionally, the service supports encryption, enabling VMs to be secured in a variety of ways. For example, the hard drives can be encrypted with BitLocker, access to the console can be restricted, and you can define the Hyper-V hosts on which a secured VM is allowed to start.
With HGS, you can protect Hyper-V servers running Windows Server 2016 and 2019 in the Datacenter edition. Older versions or Windows Server 2019 Standard edition cannot be secured with HGS. On the VMs, you again have the option of running 2012 and 2012 R2 in addition to Windows Server 2016 and 2019. Windows Server 2019 Datacenter and the free Hyper-V Server 2019 also support shielded VMs with Linux. On Windows Server 2016, these encrypted VMs can only be used with Windows Server 2016. In addition to this new feature, Microsoft has further improved the technology behind shielded VMs. Thanks to the offline mode, they now still start if the HGS cannot be contacted.
To use shielded VMs, you first need a server or cluster with the HGS. In addition to Hyper-V, you also have to install the Host Guardian Hyper-V Support server feature on the Hyper-V hosts to be protected. This extends the functions of Hyper-V to include options for operating shielded VMs.
You also need to install the Remote Server Administration Tools (RSAT) for shielded VMs when you install the Hyper-V host and connect to the Host Guardian Service. Known as Shielded VM Tools , they are not automatically installed on Hyper-V hosts but have to be set up manually.
When you create new shielded VMs, they are of the "generation 2" type. HGS uses a virtual TPM (vTPM) chip for protection. The Add-VMTPM PowerShell cmdlet is also useful for this purpose. The tools needed to connect Hyper-V to the Host Guardian Service can also be installed in PowerShell:
Install-WindowsFeature -Name HostGuardian Install-WindowsFeature -Name RSAT-Shielded-VM-Tools Install-WindowsFeature -Name FabricShieldedTools
You can handle the task of securing the Hyper-V hosts, for example, through membership in an Active Directory group if you do not rely on UEFI and TPM. Use the cmdlets:
Get-WindowsFeature HostGuardian Get-HgsClientConfiguration
to check whether a host is already connected to an HGS server.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)


