Articles
Stopping SQL Injection
SQL injection can strike at any moment. GreenSQL is an effective remedy that sits between the database and application and filters out suspicious queries.
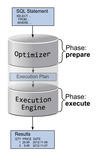
Optimizing SQL with Execution Plans
Understanding database execution plans is the key to assessing effectively the optimum potential of an SQL query or estimating your future resource requirements.
Fedora 18 for Admins
Fedora is a trend-setting distribution that sets the pace for future developments of Red Hat Enterprise Linux. Administrators, regardless of whether they use Fedora, are well advised to look at the newest innovations of the Fedora distribution.
Windows Server 2012 Tricks
Users of Windows Server 2012 will benefit from numerous innovations, especially in the areas of virtualization, high availability, and storage. In this article, we show you some tricks that make handling the new system much easier.
Ubuntu Desktop Remix
Ubuntu Business Desktop Remix sees Canonical not only attempt to oust Windows off the enterprise desktop but also position itself as a low-budget alternative to enterprise desktops by Red Hat and SUSE.
Top PowerShell Cmdlets
Windows is no longer the system for mouse pushers. In the latest server version, the default installation installs without a GUI, and management via PowerShell is a part of everyday life for Windows administrators.
Pen Testing with netcat
Once you have successfully exploited a target machine, you might be faced with a dilemma common among penetration testers: Do I have shell access or terminal access? These are not the same, and careful knowledge must be used when interacting with a shell compared with a terminal.
Configuration Management with puppet
If you really want your evenings to belong to your job, you don’t need to depend on configuration management. But is all your overtime really necessary just to configure a server system? Configuration should just happen by magic these days; after all, we’ve had computers long enough to understand how to get it right.
Forensic Analysis on Linux
In computer forensics, memory analysis is becoming increasingly important as a means for investigating security incidents. In this article, we provide an overview of the various memory dumping options on Linux and introduce the support in Linux for the Volatility Analysis Framework.
Access Anywhere with Mobile IPv6
IPv6 includes Mobile IPv6, a new standard for communication with mobile devices, which ensures permanent accessibility regardless of your current location. In this article, we provide an overview of Mobile IPv6 functionality.
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.