Articles
Centralized Password Management
Time and again, situations arise in which admins need access to a system they do not otherwise manage. But, do you want to hand over responsibility for password management to a centralized software? What capabilities must that software have?
IPRoute2: arp, route, and ifconfig in a Single Tool
Traditional administration command-line tools such as ifconfig, route, and arp are almost as old as TCP/IP itself. We provide an overview of how the IPRoute2 toolkit now unifies the management of kernel network components.
Secure Alternative to FTP
Although FTP still does loyal service despite its age, if you need to send sensitive data, you should consider managed file transfer.
Speed up Your Name Server with a MySQL Back End
PowerDNS is a secure, scalable, and reliable DNS server solution licensed under the GPL. We show you how to create a primary server with a MySQL back end managed by a Poweradmin web GUI.
Red Hat’s Cloud Tools
Red Hat massively expanded its cloud portfolio during 2012. This overview can help you evaluate Red Hat’s products in the context of VMware and others.
Mail Helpers: Improve Your Email Experience with These Handy IMAP Extensions
A set of protocol extensions keeps the legacy IMAP 4 protocol usable, which also helps mobile clients. We present a healthful mix of useful extensions.
PowerDNS: The Other Open Source Name Server
PowerDNS is an amazing, feature-rich, and versatile DNS server option.
Stopping SQL Injection
SQL injection can strike at any moment. GreenSQL is an effective remedy that sits between the database and application and filters out suspicious queries.
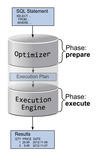
Optimizing SQL with Execution Plans
Understanding database execution plans is the key to assessing effectively the optimum potential of an SQL query or estimating your future resource requirements.
Fedora 18 for Admins
Fedora is a trend-setting distribution that sets the pace for future developments of Red Hat Enterprise Linux. Administrators, regardless of whether they use Fedora, are well advised to look at the newest innovations of the Fedora distribution.
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.