Virtualization with KVM
All for One
Whether you want to lock up your web server, test security functions, put a really powerful server to better use, or just try out a new distribution, virtual machines can be very useful. The Kernel-based Virtual Machine (KVM) [1] is a fairly recent project now being promoted by Red Hat, and it's another candidate for the job of launching and managing your virtual machines. Although KVM is frequently overlooked in the wake of Virtualbox and VMware, it offers an impressive feature scope, is included by nearly every distribution, and is totally free. The virtualization functions in Red Hat Enterprise Linux are based on it.
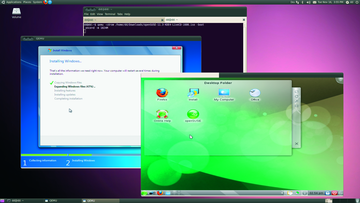 Figure 1: Thanks to KVM, Windows 7 and openSUSE 11.3 will run peacefully side by side on Ubuntu 10.04.
Figure 1: Thanks to KVM, Windows 7 and openSUSE 11.3 will run peacefully side by side on Ubuntu 10.04.
Building Blocks
KVM comprises individual modules that handle different tasks. To start, Qemu [2] emulates the hardware of one or multiple computers. Operating systems can coexist peacefully on the virtual machines that Qemu provides without fighting over the physical network interface (Figure 1).
Of course, simulating computer components is heavy on CPU cycles. To improve the execution speed of the guest operating systems, Qemu hands over some management tasks to the kernel driver developed by the KVM project. Among other things, the driver ensures efficient memory management and runs the programs on the virtual machines directly on the physical processor. To allow this to happen, the driver relies on the advanced instruction sets provided by state-of-the-art processors such as Intel VT or AMD-V. Because Qemu only has to worry about emulating a couple of hardware components, the guest operating systems are nearly as complete as on the physical computer. Figure 2 shows how KVM and Qemu interact.
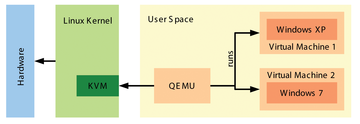 Figure 2: Overview of KVM architecture: Qemu juggles the virtual machines accesses the KVM driver for some tasks. A kernel that provides this custom functionality is referred to as a hypervisor.
Figure 2: Overview of KVM architecture: Qemu juggles the virtual machines accesses the KVM driver for some tasks. A kernel that provides this custom functionality is referred to as a hypervisor.
Basically, any software could use the infrastructure that KVM provides. But right now, only Qemu actually has this ability. Because the competitors all provide their own kernel modules, this situation likely will not change, at least not in the near future. And, if you decide to use the KVM and Qemu team, you can't run VirtualBox or VMware at the same time because of conflicting modules.
Numbers
If you are thinking of deploying KVM and Qemu, you need a CPU with Intel VT or AMD-V. You can discover whether your computer has this technology with a simple command:
egrep -c '(vmx|svm)' /proc/cpuinfo
The result must be greater than 0 (Figure 3). If not, either the processor doesn't support the special commands, or the commands have been disabled in the computer's BIOS. Users with Intel processors can additionally check their model's capabilities [3]. Qemu will actually run without processor support, but doing so slows the virtual machines down to a crawl.
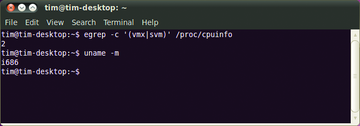 Figure 3: During testing, the CPU at the required advanced instruction set (2), whereas the 32-bit Ubuntu (i686) can only run 32-bit systems.
Figure 3: During testing, the CPU at the required advanced instruction set (2), whereas the 32-bit Ubuntu (i686) can only run 32-bit systems.
If you want to launch 64-bit operating systems on your virtual machines, the Linux host system must provide a 64-bit kernel. To determine this, run the uname -m command, and it should output a value of x86_64 or amd64. You can run virtual machines with 32-bit operating system and 64-bit system,but not the other way round. Using a 64-bit kernel as your basis also has the advantage that you can use more than 4GB RAM. Thus, you can run several more virtual machines or assign more memory to the existing machines.
Luckily, KVM became an official component of all Linux kernels as of version 2.6.20. In other words, you only need to install Qemu and a couple of tools. Most distributions provide a compact meta-package that lets you do so. On Ubuntu Version 10.04 or later, the package is called qemu-kvm (and not kvm-qemu in contrast to what the documentation maintains); in openSUSE 11.3, the package is simply called kvm.
Building a House
The next step is to create a home for the future guest system. To do so, you can either provide a physical hard disk reach operating system, or you can choose the low-budget approach and use images. The latter works similarly to ISO files for CD-ROM: While the operating system on a virtual machine thinks that it is working with a physical hard disk, Qemu actually packs all the data into a giant file. You can back up the hard disk image like this with any backup program and quickly copy it to another machine, or you can replicate it on another machine, without needing to launch a partitioning program. A new blank image is easily created using qemu-img:
qemu-img create -f qcow2 windows.img 30G
This command creates a new hard disk image with a name of windows.img in the qcow2 format; the image can store a maximum of 30GB of data. The advantage of the qcow2 format is that it grows dynamically to reflect the content. In other words, the image is only as big as a file that it contains. But, because an image really can reach its maximum size limit, you should make sure you have at least 30GB of free space on the physical disk. Qemu can also use images created by its competitors VirtualBox 1.1, VirtualPC (.vhd file extension), and VMware (.vmdk file extension). You can also use disk images with uncompressed raw data created by, say, the dd tool.




