Lead Image © Nah Ting Feng, 123RF.com
Detecting system compromise
Foundational Security
The cybersecurity landscape is large and constantly evolving. System providers incorporate a variety of security mechanisms into their systems, and many more security mechanisms and services targeting home or enterprise are available for purchase. The services share the common goal of preventing or detecting system attacks, or both. A newcomer has emerged in the commercial cybersecurity space called runtime integrity that promises not only the ability to detect when a system is attacked, but also to provide strong evidence that systems – even vulnerable systems in the face of dreaded zero-day attacks – have not been compromised.
False Sense of Security
Every day people access their various computing devices for a multitude of reasons, some critically important to their work or personal lives. So pervasive are these devices that virtually no aspect of life is independent of them. The devices themselves depend on the vast Internet for access to the computing resources and services needed to perform their functions.
Despite a huge reliance on computers, you seldom stop to consider whether they are up to the task. You implicitly rely on the idea that device manufacturers have incorporated appropriate protection mechanisms to make them trustworthy. Similarly, you assume installed application software is safe to use, correctly performing its desired functions and only those functions. Your decisions as to which systems and software to deploy become implicit statements that you sufficiently trust them to do the job throughout the life of the system.
When you do acknowledge the reality of exploitable system vulnerabilities, previously known or yet to be discovered, you seek solace in the idea that current cybersecurity practices can somehow protect systems – or at least limit damage – by:
- applying the latest software security patches,
- restricting system access with the latest access control and authentication mechanisms,
- implementing encryption to ensure data is protected while in transit and when stored,
- employing monitoring to warn whether anything out of the ordinary is occurring, and
- relying on training to prepare system users not to engage in unsafe practices that might compromise system security.
However, are current cybersecurity best practices enough?
In short, the answer is "no." History teaches that exploitable vulnerabilities always surface, and even the most careful users can sometimes be tricked into actions that allow attackers access. System attacks can have potentially great consequences, including data loss or exposure, lost productivity, interruption of service, and all the associated monetary costs for recovery. Additionally, system attacks damage confidence that systems are suitable for their intended tasks.
The result of successful attacks are sometimes immediately obvious, but more insidiously, the effect can persist long after the initial exploit, leaving no visible trace that the system is not as it was before and is unsafe to use. Runtime integrity, a more effective integrity system capable of detecting attacks on a running system and identifying system modifications, can be an important tool to maintain confidence in your systems.
Integrity Systems
To understand runtime integrity, it is instructive to delve into the general idea of system integrity , an idea that has been around for many years. Simply put, system integrity is an idea that the system is exactly as it is expected to be and that it has not been modified in any unauthorized manner. It follows that if the system has not been modified, it will function just as it initially did.
Integrity systems are the mechanisms that generate, and subsequently evaluate, evidence that can be used to substantiate assertions that a system's integrity is intact. Integrity systems become useful when validated integrity assertions can be presented for use in security decisions that could be negatively affected when the system has been modified from its expected state. They certainly can be valuable when used for local decisions about a system but become much more powerful as a means of projecting trust across a network when integrity evidence can reliably be presented as input to remote security decisions.
At a high level, integrity evidence should be considered a characterization of a system's health. Integrity systems examine a target system, recording observations and presenting them as statements of system health that can be evaluated, with results reliably being presented as inputs to security decisions. As is the case in medical health, what constitutes "healthy enough" is subject to the context in which the question is asked. Healthy enough to attend school is an altogether different question from healthy enough for space travel.
So too with system integrity. System health depends on specific use cases, and effective integrity systems must be capable of producing characterizations with sufficient information for situational assessment. Failure to include all relevant information will likely result in erroneous security decisions. Runtime integrity is an advancement over prior integrity systems in that it yields much better system characterizations customizable for a broad range of integrity use cases.
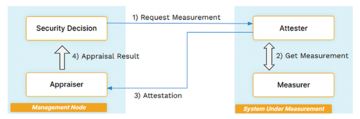
Integrity systems produce system characterizations as integrity evidence, called measurements , through a process called integrity measurement , which is a privileged function that must have a suitable vantage point to measure the target (Figure 1). Measurements must be produced in a reliable way and protected from unauthorized modification. Integrity systems assess measurements through a process called appraisal , presented through a process called attestation .
Like measurement processes, appraisal processes must consider all relevant portions of the measurement report required to support intended use cases, and attestation processes must be protected to ensure measurement reports are reliably delivered for appraisal unmolested. Failure in any of the three components would compromise any subsequent security decisions.
It's possible to combine the parts of an integrity measurement system – measurement, attestation, and appraisal – in a variety of ways, resulting in different kinds of systems with varying amounts of effectiveness. For example, they could all be co-located with the target system, with the system itself used for the needed access and resources. Alternatively, they might be located near the target system in a connected device or isolated in a virtual environment for protection from system attack. Distributing different measurement processes across different components of a more complex system even becomes possible for an eventual joint appraisal.
Appraisal might be physically separated from measurement, placing it where remote security decisions are being made. Appraisal might also be off-loaded to third-party appraisal systems specializing in integrity decisions that can either be forwarded directly as inputs to security decisions or incorporated into some sort of integrity token returned to the attesting system to be presented when needed. Security mileage can vary a lot depending on how the combinations are made and protected.
The Value of Integrity
Integrity measurement and appraisal done properly can be an indispensable tool to maintain confidence in a system's health, but it also is an excellent means to improve the quality of security decisions. Confidence in security decisions rests heavily in confidence of the inputs to them and is certainly bolstered by increased confidence that the system responsible for providing those inputs has not been corrupted.
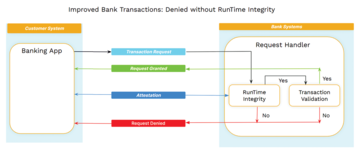
Many possible security decisions would benefit if augmented with integrity input. Any access control or authentication decision can be made more robust if, in addition to the traditional inputs to the decision, a reliable statement that the systems involved in presenting credential information or executing cryptographic protocols were not compromised. This applies to any decision involving the access of resources – a request for services, the release of protected information, or the release of workload data into cloud execution environments and would improve so many online activities that need to be secure, including such things as joining a network, online services like banking and shopping, digital payment technologies, blockchain applications, and remote computing environments, just to name a few (see Figure 2 for an example).
Integrity measurement is crucial to system integrity. When inadequately done, integrity evidence will be suspect. However, if done properly it leads to results that not only indicate when a system is compromised but can also tell what was corrupted. It won't necessarily tell how it was compromised, but that isn't as important as the fact that a compromise has or, just as important, has not occurred.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.