« Previous 1 2 3 Next »
Data loss prevention with Microsoft Purview
Scope of Concern
Setting Up Policies
If you want to create a new policy, press Create policy (Figure 2). First, select the data you want to protect. You can create policies based on an existing template set or choose to create a Custom entry, for which you will then need to define your own rules during the configuration. The templates let you define the details of the policies up front. A DLP policy comprises rules, which in turn comprise Conditions describing the confidential data, Actions , and Exceptions (Figure 3).
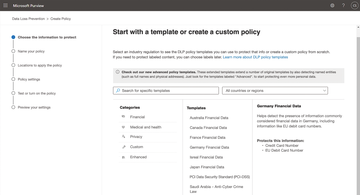 Figure 2: Microsoft Purview comes with a very extensive template set that already takes many use cases into account.
Figure 2: Microsoft Purview comes with a very extensive template set that already takes many use cases into account.
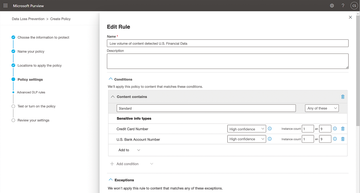 Figure 3: A policy comprises rules that define the confidential data, but also exceptions, actions, notifications, and damage reports.
Figure 3: A policy comprises rules that define the confidential data, but also exceptions, actions, notifications, and damage reports.
This example looks at German financial data and needs the appropriate template. The next step of the wizard stores the name and a short description. By default, the name and description of the template are entered automatically. The places where the policy will apply are then selected. Various areas, such as Exchange, OneDrive, end devices with Windows 10/11 and macOS, and local file shares are available for selection. Note that some locations are monitored directly after selection, but others have requirements that need to be met first. For example, monitoring local shares requires the Azure Information Protection (AIP) Scanner, and some preliminary work is also required for endpoints. I go into more detail about the requirements in the course of the article.
After choosing the locations, policy settings are defined in one of two ways. In the simpler case, you just accept the default settings from the template. Here, the wizard briefly prompts you for the data to be protected, the protections, and access settings again. A policy definition is quickly finished in this way. Alternatively, you can customize rules in more detail with the Create or customize advanced DLP rules item. A wizard is then used to configure conditions, exceptions, actions, notifications, and override rules and to create damage reports (Figure 4).
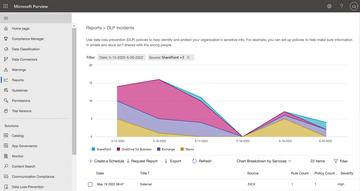 Figure 4: In addition to the warning overview in the DLP section, the Reports item offers reports with filters on DLP information.
Figure 4: In addition to the warning overview in the DLP section, the Reports item offers reports with filters on DLP information.
In most cases, you will create two content-checking rules that take specific actions according to the severity of a data breach (low or high number). By default, a low count is reached for between one and nine positive hits of a data type (e.g., credit card or social security numbers), whereas a high count is more than 10 hits.
The last step is to specify whether a rule should be enabled automatically, run in test mode first, or remain disabled. Next, you see a summary and can check and save the DLP policy, after which the policy is ready for action.
User Device and Scanner Overhead
The big advantage of Microsoft DLP is that it can be configured in one place for a wide variety of locations, including local user devices. A separate license might be required for this, as described in the "Keeping Track of Licensing" box, but that's not all, because the user devices first need to be integrated. You have several ways to do this, such as Group Policy, Intune, Endpoint Configuration Manager, a virtual desktop infrastructure (VDI) onboarding script, or a local script. I will use a local script for onboarding available under the Settings section in Purview.
Keeping Track of Licensing
As with all cloud services, if you want to use a feature, you need a matching license – and the devil is in the details, because different licenses are required depending on which location you want to monitor. Office 365 and Microsoft 365 E3 already include DLP protection for SharePoint Online, OneDrive, and Exchange Online. However, an E5 license is required to monitor team chats. If necessary, you can order add-ons for existing licenses to use the full functionality. When monitoring local services, note that all users at the location require a license, not just the user of the scanner. A detailed check is necessary, and Microsoft provides a license overview for the required compliance services [4].
The device appears in the device overview after a while. Details of the Endpoint DLP settings can be found in the matching tab on the Data Loss Prevention page. You can enable the Advanced classification scanning and protection feature here, too. Because content is sent from the local device to cloud services for scanning and classification, a bandwidth limit can be configured here. Additionally, you can set file path exclusions and detail restrictions.
Setting up scanning for local directories is a little more complicated. First, the Azure Information Protection Unified Labeling Client needs to be installed and configured. It then connects to the Azure Information Protection extension on the Azure portal and adds the repositories to the content scan job. The procedure is described in detail in the documentation [5].
Policies in Action
Before activating a DLP policy, you need to Test it out first . In this way, you can check the policy by looking at the policy tips, alerts, and activities. Outlook online and Outlook as of version 2013 directly show you notices relating to rule violations (Figure 5). On the one hand, you get to see the unauthorized recipient, and on the other, you can view references to the confidential information.
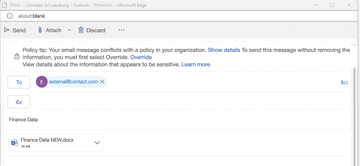 Figure 5: Policy tips alert the user to violations at an early stage and offer the option of overrides, like this one in Outlook.
Figure 5: Policy tips alert the user to violations at an early stage and offer the option of overrides, like this one in Outlook.
If an employee attempts to send a sensitive email message from an older Outlook client, Exchange Online will respond with an undeliverability report, or at least document the email, depending on the configuration and severity of the violation. For documents in OneDrive and SharePoint, policy tips show up as warning icons on the individual entry. Teams directly adds a notice to the message. Not only in the applications, but also on the end device, hints can be displayed for various file actions.
The Compliance Manager can be notified directly of the incident by email, as mentioned earlier. You can define the scope of the information in a status notification in the rule settings. If required, the original email can also be sent. Alerts also appear in the DLP alert management dashboard. If you click on an alert there, an area opens up on the right making it very easy to see what happened, who was responsible for the action, and what policy applied.
The Show details link opens the alert and shows the content in more detail. Additionally, detailed information about the incident is displayed, and actions can be performed as a function of the incident. For example, data found on OneDrive can be deleted or sharing of the data blocked. The DLP alerts overview also acts as a simple case management system, and you can assign alerts to a user. You can manage the entries with the status Active , Investigating , Dismissed , or Resolved .
Purview also has an area for reports, including DLP incidents , DLP policy matches , and False positives and overrides . The reports can be requested by email and exported in Excel format, and you can create a schedule and have reports sent to you on a weekly or monthly basis.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







