« Previous 1 2 3 Next »
Real World AWS for Everyone
Cloud Config
Amazon offers a comprehensive portfolio of public cloud services. The options cover the spectrum from IaaS, to PaaS, to SaaS to managed services. Due to the impressive usability, even small companies without available cloud experts find it easy to get started. In all, Amazon Web Services (AWS) [1] offers well over 50 cloud services, roughly divided into categories such as data processing and storage, database, and migration [2]. Amazon's services are similar to Lego bricks; you can combine them using a simple management console GUI to build virtual networks with different properties. You can also churn up Amazon services through a command-line interface or trigger them programmatically using the provided APIs. This article describes how to implement a web server with a high-availability back-end database in the Amazon cloud . The configuration is similar to the scenario depicted in Figure 1. A NAT server will provide connectivity with the Internet. The database is via Amazon's Relation Database Service (RDS).
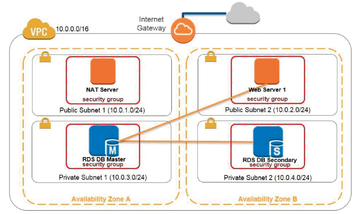 Figure 1: Web server with a back-end, high-availability database: The scenario described in this article.
Figure 1: Web server with a back-end, high-availability database: The scenario described in this article.
Terms and
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







