
Lead Image © Tjefferson, 123RF.com
Virtual networks with Hyper-V in Windows Server 2016
Network in a Box
Microsoft expands Hyper-V's functionality in Windows Server 2016. One interesting new feature is that Hyper-V containers are included in Technical Preview 4 (TP4), which let you virtualize Docker in Hyper-V.
In Windows Server 2016, you can add and remove network adapters on the fly (Figure 1). You do not need to shut down VMs to shut down an adapter. This feature is particularly useful if you work with different VLANs or network segments and need a way to connect VMs to networks quickly and easily. But this feature only works with generation 2 VMs. You need to decide when you create a virtual server whether you want to use these options because you can no longer change the generation retroactively.
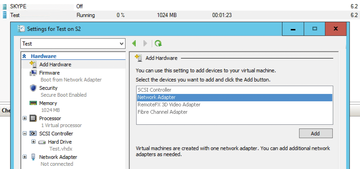 Figure 1: Windows Server 2016 lets you add or remove network adapters on the fly – to or from generation 2 VMs.
Figure 1: Windows Server 2016 lets you add or remove network adapters on the fly – to or from generation 2 VMs.
Embedded virtualization (nested virtualization) is possible in Windows Server 2016, as of TP4, and Windows 10 from build 10565. You can thus install Hyper-V on a virtual server, which you virtualized with Windows 10 or Windows Server 2016, and create virtual switches. You can virtualize virtual switches again, which is useful not only for test environments, but also for the new Windows server or Hyper-V containers. You can
...Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.








