Figure 5
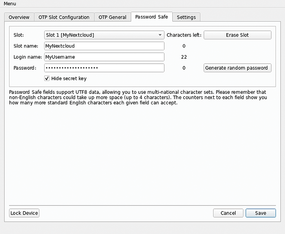
Figure 5: The User PIN may be used to retrieve a password stored within the Nitrokey. The drawback of this approach is that, once the Nitrokey gives the password over to the operating system, it could be stolen if the operating system is compromised.