Figure 1
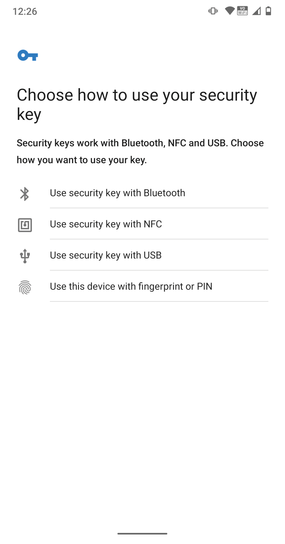
Figure 1: Selecting an authenticator on the smartphone.

Figure 1: Selecting an authenticator on the smartphone.