Figure 4
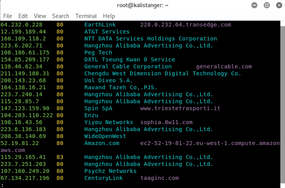
Figure 4: Results of Shodan/Metasploit search.

Figure 4: Results of Shodan/Metasploit search.