Figure 3
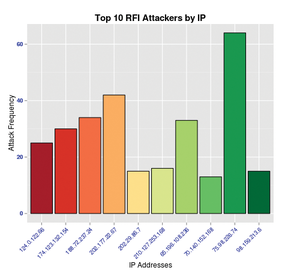
Figure 3: Histogram plot of RFI Top 10 attacking IP addresses.

Figure 3: Histogram plot of RFI Top 10 attacking IP addresses.