« Previous 1 2 3 Next »
Security analysis with Microsoft Advanced Threat Analytics
Under the Radar
Establishing the ATA Infrastructure
ATA comprises gateways that collect the information on the network and perform analyses. The general layout of an ATA infrastructure is not complicated. You first install the ATA Center on a server on your network. The installation wizard is a fast point-and-click experience. Microsoft ensured that provisioning the solution takes just a couple of minutes.
The ATA Center is the central management tool that collects all the information from the environment. You can connect various gateways to an ATA Center. To establish the environment, you thus ideally need multiple servers, but you can complete the entire installation on a single server. After completing the installation, ATA generates some rules of its own and analyzes the network, with no need for additional configuration or data updates – ATA works completely autonomously. Once the software has learned your users' habits, it can quickly identify unusual user behavior. The longer you operate the system, the more it learns.
Make sure you enable the necessary ports between the servers and for alerting administrators, which means the ports for SSL (443), HTTP (80), and HTTPS (443). One ATA gateway must be able to see all your network traffic. For this to happen, you need to set up port mirroring for each domain controller (DC) you want the tool to monitor. Microsoft describes the precise system requirements on TechNet [2].
After meeting all the requirements, you then install the ATA Center. In the course of doing so, you also define the database size, the IP addresses, and other important settings. However, these details are fairly trivial. At the same time, you store the certificates for secure connections (Figure 2). In a lab environment, you can work with self-signed certificates. The Center Communication IP Address:Port can be set to the IP address of the management website during the setup. The important thing here is to use a different port.
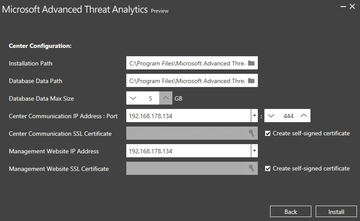 Figure 2: The wizard for installing the ATA center lets you configure important settings and store the required certificates.
Figure 2: The wizard for installing the ATA center lets you configure important settings and store the required certificates.
ATA uses the free MongoDB database to store the data. By default, this resides in the %programfiles%\Microsoft Advanced Threat Analytics\Center\MongoDB\bin\data directory. The wizard stores the system files in %programfiles%\Microsoft Advanced Threat Analytics\Center. After using the wizard to set up the ATA Center, you need to open a connection to the console via the web interface. To do this, enter the IP address or name of the Center in your web browser. After logging in to the Center, you can manage the ATA environment in this console. Then, the main window will show you suspicious attacks and the actions that have occurred. First, however, you need to complete the configuration of the environment. To do so, you need the ATA gateways that investigate the network itself.
Configuring the ATA Gateways
After installing and setting up the ATA Center, you can access its management page by clicking the button on the server desktop or surfing to https://<server name or IP address>
. After installing in a production environment, or in case of errors, you can check out the logfiles for troubleshooting. The file Microsoft.Tri.Center-Errors.log resides in %programfiles%\Microsoft Advanced Threat Analytics\Center\Logs.
The ATA Center and the ATA Gateway both run as services. Thus, you need to check that both of these services are running for the environment to work. You can also monitor ATA with the Windows Performance Monitor. To allow this, Microsoft has added the NetworkListener Captured Messages/sec and EntityTransfer Activity Transfers/sec features. For more information, check out the TechNet forum on ATA [3].
The next step is to configure a first ATA gateway (Figure 3). To log in to the ATA Center, use either a domain administrator account, the local administrator account, or an account that you added to the local Microsoft Advanced Threat Analytics Administrators group. The fastest way to start local user management is to type lusrmgr.msc . In the web interface, change to the settings. Use the Gateways section to define the login credentials under Domain connectivity settings . The gateways will use these later on to register with the ATA Center. You can either use separate user accounts or an administrative account.
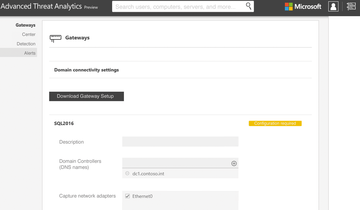 Figure 3: In the course of installing ATA, you connect the ATA Center and Gateway in the web interface.
Figure 3: In the course of installing ATA, you connect the ATA Center and Gateway in the web interface.
In the web interface, you can also download the required installation files for the gateways directly off the web. Basically, you install the gateway like the ATA Center by extracting the ZIP file and running the installer. You can also use the installation file on multiple gateways. If you want to install multiple gateways, simply copy the installation files to a share on the network. In smaller environments or lab environments, you can run the gateway and the Center on the same server. If needed, you can install more gateways at any time and add them to the system.
In the course of the installation, you need to log the gateway onto the Center. To do so, enter the username and password in the window. You also have the option of configuring the gateway with self-signed certificates. After completing the install, you can also launch the ATA Center management console from the gateway. This is a good way to test the connection between the gateway and the Center. The gateway installation files are located in %programfiles%\Microsoft Advanced Threat Analytics\Gateway.
After you install a gateway, it appears in the ATA Center management console. You can open the management tool via the gear icon at the top right in the console. All gateways are then found via the Gateways menu item. After registering a gateway, you then need to configure its settings. To do this, the web interface shows you a Configuration required button. If you deploy multiple gateways, you can also synchronize the settings at this point.
The important thing is to add a DNS server to your AD, define the network interface, and select a suitable IP address, which the gateway locks onto and monitors. Via the Center, you can configure the URL for management and the IP endpoint for the gateway connections. You also configure a number of other settings on detection. For example, you can use the Alerts item to define how ATA should alert. You have the option of defining an email server or syslog server here, although these settings are optional (Figure 4). After completing the configuration, ATA is now set up and can protect your network. The setup can also be done on virtual servers.
Managing Alerts in the Console
The ATA Center's management page shows detailed information and provides this information interactively. You are thus given an in-depth analysis of user accounts and the detected attacks. You will also find charts and a list of threats, as well as suspicious actions performed by users or attackers. You see the time at which they occurred, the resources, and the account used.
To access this information, right-click on the Alerts icon in the management interface. The interface then shows you the number of different alerts on the left, with the details in the middle of the window; you can click your way through them. At the top, you will also find a search field that lets you search for specific users or computers.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)






