Monitoring network traffic with ntopng
Eyes on the Network
Working with ntopng
Ntopng offers an enormous range of functions. For an easier start, I first take a look at the basic concepts, each of which is represented by its own menu item in the web interface. Under the Interfaces menu, ntopng lists all network interfaces built into the hardware, including not only physical interfaces like LAN and WiFi network interface controllers (NICs), but also logical interfaces like the loopback adapter.
In Hosts | Host Pools , ntopng monitors the traffic on the selected network interface cards and identifies systems that are sending and receiving packets on the network. Each IPv4 and IPv6 address that ntopng identifies is therefore interpreted as a separate host. The IP address tells ntopng whether it is a local or remote host. For local hosts only, additional information (e.g., the web pages visited, DNS requests, and the Layer 7 protocols used) are recorded.
The hosts can be grouped in host pools (Figure 2) so the cumulated traffic can be evaluated across a group of hosts. The filters in the Host menu let you further restrict the information displayed (Figure 3). In addition to hosts and host pools, MAC Addresses , Countries , and Operating Systems are also available as filters.
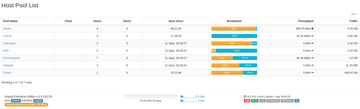 Figure 2: Host pools group devices on the network into clearly arranged groups. Ntopng then cumulates the traffic of all systems in the group.
Figure 2: Host pools group devices on the network into clearly arranged groups. Ntopng then cumulates the traffic of all systems in the group.
A "flow" in ntopng-speak is a bidirectional communication channel between two hosts. The Flows menu displays the data traffic between two hosts in real time (Figure 4). Moreover, ntopng can react to certain events and sound an alarm if previously defined threshold values are exceeded. For example, ntopng generates an alert as soon as a new device appears on the network for the first time, a status change on a switch port is detected by SNMP, or a system contacts a malware host.
Additionally, all activities of users logged on to the web interface are also registered as alarms. In this way, failed logon attempts, for example, can be traced. Alerts are displayed on the Alerts dashboard (reached from the Alerts icon – the warning sign – at the top) but can also be processed further – more about this later.
Traffic
Now that you are familiarized with the basic functions of ntopng, I'll take a look at the system in practical use. When you log in to the web interface, ntopng loads the traffic dashboard by default (Figure 1). All the information visible in the web interface always relates to the current state of the network. In the table on the left side of the screen you can see the "top talkers" (local and remote), which are the systems currently causing the most traffic.
The two upper graphs on the right side show the current load for the selected network interfaces and break down the traffic by applications (e.g., SMB, TLS, POP). The two lower graphs contain the same data, but for the last 24 hours. You can access the data from previous periods by clicking on the Traffic icon and selecting the Traffic Report option. When you get there, you can either specify the exact time period you want to analyze or use shortcuts to select, say, an hour, day, or month as the period.
Traffic Profiles
With the help of traffic profiles, network traffic can be evaluated in a very specific way at both the network and application level. For example, if you want to know how much traffic an individual (or all) host generates specifically through the use of YouTube, Facebook, or Wikipedia, traffic profiles are the right tool for this. You can also check how much traffic a particular MAC address is causing or what device on the network is still communicating with the outdated and insecure SMBv1 protocol.
The syntax for traffic profiles is based on the Berkeley Packet Filter (BPF) format, which tcpdump also uses. You will find the traffic profiles in the Settings menu; some examples are also listed here. The application protocols detected by ntopng can be determined by entering the command:
ntopng --print-ndpi-protocols
The desired application protocols are referenced in traffic profiles by means of the corresponding index number. A traffic profile for identifying the data stream to the Wikipedia website can be created with the l7proto 176 command, but the network traffic between the IP addresses 192.168.0.9 and 192.168.0.224 can be aggregated as follows:
ip host 192.168.0.9 and 192.168.0.224
Ntopng applies the traffic profiles to the flows; accordingly, the evaluation feature is found in the Flows menu.
Buy this article as PDF
(incl. VAT)







