Secure remote access and web applications with two-factor authentication
Ticket Control
Client/Server Model
All OTP systems rely on the client/server model. The front end is the client in the form of the OTP tokens; the back end is a server system that verifies the one-time passwords and authentication information of the users and then passes it to the appropriate application via an interface.
The universal interface is often the RADIUS protocol (Remote Authentication Dial-In User Service), which most applications can handle. Of course, the back end can be a cloud application instead of a dedicated service running on a server. The best known example of this kind of two-factor authentication is probably Google Authenticator.
Two-factor authentication solutions are in principle not limited to specific application scenarios. In practical applications, however, their use has proved valuable in two areas in particular: the authentication of remote access connections and web applications. Especially in web applications, the use of two-factor authentication is almost unavoidable because, unlike VPN and SSH connections, client-side certificates are almost never used to ensure authentication of the client by the server.
In the simplest case, a sniffed password is all it takes to take over the account – for example, by means of a man-in-the-middle attack, a replay attack, or classic network sniffing. Also, the number of web applications is growing so fast that an average user already uses 10 to 15 web applications every day. Just think about the many social networks, webmail, banking applications, e-commerce, and information portals visited every day.
Securing Google Services
Google primarily developed Authenticator to add strong authentication for access to its applications. This authentication method, also known as "two-step verification," can alternatively rely on SMS or a voice call (Figure 2). The Authenticator app, however, can also authenticate non-Google services, as I shall describe later.
To enable strong authentication in your Google account, go to https://accounts.google.com/SmsAuthConfig and enter the phone number of your smartphone. Google sends a link to this number that lets you download the Google Authenticator app. Next, in the account settings of your Google account, select the device, such as iPhone , on which you installed the app. In the app, tap the plus sign and choose the Scan Barcode command.
Now scan the bar code displayed in your Google account and type in the code displayed in the app to complete the setup in two steps (Figure 3). To be on the safe side, you should print the substitute codes [14], which you can use to log in to your Google account if you lose your cellphone.
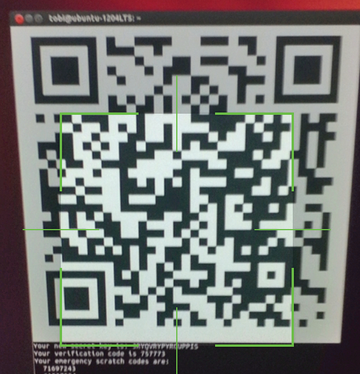 Figure 3: After scanning a QR code from the screen, the Google Authenticator app is then associated with the user account.
Figure 3: After scanning a QR code from the screen, the Google Authenticator app is then associated with the user account.
Dropbox with Google Authenticator
Fewer people will be aware that Dropbox recently introduced support for strong authentication using Google Authenticator. Enabling this feature is similar to setting up the Google account. To begin, log in to your Dropbox account in your browser and select the Security tab. In the Account sign in box , click change in the Two-step verification line. A wizard will take you through the process of enabling two-step verification, via either an app or text messages. If you're verifying with an app, select Authenticate with Google Authenticator app ; then, in the app again, tap the plus sign and scan the QR code on the screen.
After entering the one-time password, two-factor authentication is enabled (Figure 4), and Dropbox shows you some substitute codes for printing.





