« Previous 1 2 3 4 Next »
Hacking Mutillidae II
Wasp Attack
Your Point Is, Caller?
Before I move on to the vulnerability that I will take to completion, I won't go into the ins and outs of SQL injection (SQLi) at this point, but you can find a well-constructed explanation on the PortSwigger site [8] if you need more information. The web page explains that SQLi "… is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database."
Very briefly, a structured query language (SQL) command looks something like,
SELECT * FROM staff WHERE member = 'chris' AND employed = 1
whereas the abuse of that SQL might look like
SELECT * FROM staff WHERE member = 'chris' or 1=1--' AND employed = 1
(note the extra characters after 'chris'). To abuse Mutillidae, you confuse the SQL instruction with a clever mix of apostrophes and dashes. On the Mutillidae login page (Figure 8), you add this strange-looking code snippet to the Username
field,
' or '1'='1'-- -
leaving the Password field blank and then clicking the Login button. Having done so, the horizontal navigation bar at the top of the screen suddenly changes from saying Not Logged In to the view shown in Figure 9, which shows that you have authenticated and, as if by magic, are the admin user.
If you click the new page icon (to the right-hand side of the red admin text), you are presented an Edit Profile page that mentions g0t r00t? , among other things. Before proceeding to the next challenge, be sure to click the Logout link on the top navigation bar.
Echo Chambers
The next attack relates to cross-site scripting (XSS), wherein a browser, or some other type of client, pushes data up to a server and manipulates it in a way that abuses the server. Usually, it's an injection of bad code into otherwise normal websites.
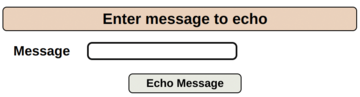
I visit the Echo Message page for this example. In Figure 10 you can see it is a standard input box, and its functionality is designed to repeat, parrot-fashion, the content submitted. In my case the URL that I use to visit the Echo Message page is:
http://localhost:8000/index.php?page=echo.php
The attack employed involves pasting the following JavaScript into the message box and then clicking the button to submit the form:
<script>alert(document.cookie)</script>
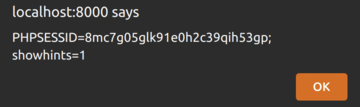
In Figure 11 you can see the resulting pop-up dialog. Gaining access to the PHP session information is the aim of this attack, so you can force the server to ingest your attack code.
You can now replay the PHPSESSID and impersonate the previous session to do bad things to the target system. An informative web page [9] states: "It is important to maintain the confidentiality of a session ID so other users or attackers do not use it to access the same account. Some web applications allow replaying (reusing) the old session ID to access the resources, without re-authenticating the user."
The page continues to explain that if the session ID is stolen, the attacker might be able to:
- keep track of a user moving around a site,
- view the user's profile or other account information, and
- impersonate the user (and spend their money, among other things).
I will leave you to explore this XSS vulnerability further. If you want some really good pointers, then click the Hints and Videos pull-down menu on the Mutillidae UI to get going. This helper applies to most sections of the Mutillidae site. The expert help sections are very well thought out, accommodating, and designed to help you learn.
This Vehicle Is Reversing
Having seen some of the more obvious vulnerabilities in Mutillidae II, I will visit the DNS lookup page (OWASP 2017 | A6 Security Misconfiguration | Method Tampering (GET for POST) | DNS Lookup ). The URL for my page is
http://localhost:8000/index.php?page=dns-lookup.php
I use a hostname for the DNS lookups that permits (in line with the Nmap Security Scanner Project usage policy [10]) some non-denial of service (DoS) type scans (i.e., scanme.nmap.org). Because I'm just doing DNS lookups, I'm really just showing you the generosity of this scanning service from Nmap.
When you enter scanme.nmap.org and click the Lookup DNS button, you will see the expected output: IPv4 and IPv6 IP address details.
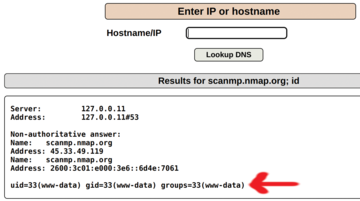
What about trying to abuse the input? Use the id command, which is supposed to show a user's details and the groups to which they belong,
scanme.nmap.org; id
to see whether it is filtered or sanitized correctly by the application. Mutillidae does indeed process the id command if you separate the hostname and the command with a semicolon (Figure 12).
Next, try a few other commands, such as pwd or ls. They work, too! Moving on, find out whether you can get any more useful functionality from this insecure page.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.