« Previous 1 2 3
Link Encryption with MACsec
Under Seal
Switch to End Device with Dynamic Key Distribution
The supplicant needs a MACsec profile. You can create this in the associated profile editor for the Cisco Secure Client by selecting MKA as the key management approach in the Networks/Security area and the encryption algorithm for MACsec. This setting must be compatible with the switch and be configured symmetrically. In this example, I choose AES128-GCM. Next, import the profile on the client. The authenticator (switch) requires a little more manual work: First, you need to define the RADIUS servers with IP addresses, ports, and a shared secret. Second, reference them in the settings for authentication, authorization, and accounting (AAA) and enable IEEE 802.1X globally if you have not already done so.
Additionally, you need a MACsec-specific MKA policy. The key server priority is set in the policy. Also, you need to specify the encryption algorithm to match that of the supplicant (i.e., AES128-GCM for the example in Listing 1) and set the Confidentiality Offset to 0 bytes in the MKA policy. This setting tells MACsec to encrypt the whole frame. Where switches are coupled, a certain portion of the frame could remain unencrypted (e.g., to allow virtual local area network (VLAN) tags to be evaluated for transit components) (Figure 3). Replay protection defines the extent to which the frame order can deviate from the regular order.
Listing 1
MACsec Downlink to Terminal Device
radius server macsec1 address ipv4 192.0.2.1 auth-port 1812 acct-port 1813 key t0ps3cr3t ! radius server macsec2 address ipv4 192.0.2.2 auth-port 1812 acct-port 1813 key t0ps3cr3t ! aaa group server radius macsec server name macsec1 server name macsec2 ! aaa new-model aaa authentication dot1x default group macsec aaa authorization network default group macsec aaa accounting dot1x default start-stop group macsec ! dot1x system-auth-control ! mka policy ITA_MKA key-server priority 100 macsec-cipher-suite gcm -aes-128 confidentiality-offset 0 replay-protection window-size 10 ! interface GigabitEthernet2/0/1 description ITA_MACsec_Client switchport mode access switchport access vlan 10 macsec authentication host-mode multi-auth authentication order dot1x authentication port-control auto dot1x pae authenticator authentication linksec policy must-secure mka policy ITA_MKA spanning-tree portfast
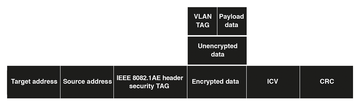 Figure 3: MACsec frame setup with encrypted VLAN tag and payload. In addition to classic Ethernet headers, the 802.1AE header (security tag) and an ICV are inserted.
Figure 3: MACsec frame setup with encrypted VLAN tag and payload. In addition to classic Ethernet headers, the 802.1AE header (security tag) and an ICV are inserted.
Finally, set up the physical port, which is used to define both the legacy 802.1X settings and a reference to the MKA policy; MACsec is enabled, and a linksec policy with must-secure enforces encryption. On the authentication server, you first need to define an authorization profile with the must-secure policy, which you then reference in an authorization policy for the desired supplicants on the basis of their properties from the authentication.
Switch to Switch in Static CAK Mode
The setup for MACsec between two switches is somewhat simpler than dynamic key distribution in the case of a switch to end device. The configuration is the same on both switches except for the key server priority. First, define a keychain for MACsec with a key number, which acts as the CKN. Inside the key number, the CKN creates the algorithm for the key and the key string, which acts as the CAK. Second, define the MKA policy (which I will not explain again here). Finally, bind the MKA policy and the keychain as a pre-shared key and enable MACsec on the physical interface (Listing 2).
Listing 2
MACsec Uplink to Switch
key chain ITA macsec key 1000 cryptographic-algorithm aes-256-cmac key-string 12345678911234567890123456789012 ! mka policy ITA_MKA_Switch key-server priority 100 macsec-cipher-suite gcm-aes-256 confidentiality-offset 30 ! interface TenGigabitEthernet1/0/1 description ITA_MACsec_Client switchport mode trunk macsec network-link mka policy ITA_MKA_Switch mka pre-shared-key key-chain ITA
Conclusions
MACsec cannot replace end-to-end encryption; however, when it comes to encrypting a defined link with high performance, MACsec is a very good choice. The same applies to securing Layer 2 protocols between client and switch or between two switches. Despite the latest revision in 2018, supplicant availability is still fairly low.
Infos
- MACsec IEEE 802-1AE: https://1.ieee802.org/security/802-1ae/
- Cisco terminology for MACsec: https://community.cisco.com/t5/networking-knowledge-base/macsec-history-amp-terminology/ta-p/4436094
- MACsec configuration on Cisco Catalyst 9300: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9300/software/release/17-6/configuration_guide/sec/b_176_sec_9300_cg/macsec_encryption.html
« Previous 1 2 3
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







