« Previous 1 2 3 4 5
Six new security features for Windows Server 2022
Shielded
Fine Tuning with Group Policies
As an alternative to WAC, you can control the functions of the Secured-core server through group policies. The options are found in the Group Policy Management Editor under Computer Configuration | Policies | Administrative Templates | System | Device Guard . Use the Turn on Virtualization Based Security setting when you get there.
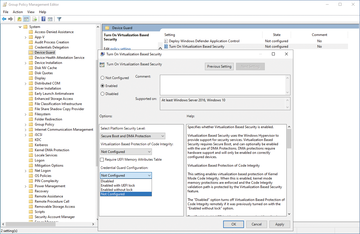
If you enable this setting, four drop-down boxes in the options area control the details (Figure 2). The first option for the platform security level enables Secure Boot with or without DMA protection. Not Configured means that the group policy will not change the HVCI status already in place on a target machine. Enabled without lock is equivalent to the state that you can enable in WAC. HVCI is enabled in this case and can also be disabled again with a group policy. The Enabled with UEFI lock option links the HVCI status to the target's local UEFI, if compatible. In this case, the function can no longer be disabled remotely, whether by WAC or by group policy.
The memory attributes table checkbox ensures that VBS and HVCI are only used on systems with a compatible UEFI. Microsoft otherwise warns about crashes, data loss, or incompatibility when you install physical expansion cards. Credential Guard is not one of the six core functions of the Secured-core server, but it uses VBS as a basis for protecting credentials. The options are identical to those of HVCI. Credential Guard can also be connected to a local UEFI. Finally, the Secure Boot configuration option controls whether or not system monitoring should be enabled.
In Computer Configuration | Policies | Administrative Templates | System | Kernel DMA Protection you find Enumeration policy for external devices incompatible with Kernel DMA Protection . This setting decides whether the target system generally blocks or allows devices whose drivers do not support DMA remapping. By default, the third option specifies that these devices only work as long as a user is logged in and the screen is not locked.
Conclusions
Secured-core server uses all the security features of modern hardware and virtualization infrastructures. Provided UEFI and device drivers are suitable, the setup involves just a few steps. Secured-core server reduces the attack surface of Windows Server 2022 at no additional cost and with the least possible overhead.
Infos
- OEM process for Secure Boot: https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/oem-secure-boot
- Using TPM on Windows: https://learn.microsoft.com/en-us/windows/security/information-protection/tpm/how-windows-uses-the-tpm#tpm-in-windows
- Root of trust for protecting Windows: https://learn.microsoft.com/en-us/windows/security/threat-protection/windows-defender-system-guard/how-hardware-based-root-of-trust-helps-protect-windows
- Kernel DMA protection for Thunderbolt: https://learn.microsoft.com/en-us/windows/security/information-protection/kernel-dma-protection-for-thunderbolt
- Virtualization-based security for Windows: https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.security.doc/GUID-CE292D3F-D4AC-4607-B262-DE19CE6E9F6B.html
- Configuring a key provider: https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.security.doc/GUID-3D39CBA6-E5B2-43E2-A596-B9A69B094558.html
- Trusted launch: https://learn.microsoft.com/en-us/azure/virtual-machines/trusted-launch
- WAC download: https://www.microsoft.com/en-us/windows-server/windows-admin-center
- Configuring single sign-on: https://learn.microsoft.com/en-us/windows-server/manage/windows-admin-center/configure/user-access-control#configure-single-sign-on
« Previous 1 2 3 4 5
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.